Photographer – Offsec PG Play

Lets start by gathering our nmap scans. I always do a basic nmap and a detailed nmap scan.
nmap -T4 -p- 192.168.187.76
nmap -A -O -p 22,80,139,445,8000 192.168.187.76
As we can tell from the detailed nmap scan, we have a web server on port 80, ssh on 22, smb on 139/445, and a second web server on 8000. Further this is a Linux machine.
Lets start with the smb service. I started to enumerate this service with netexec. I ran an initial search through with a null session and found that I had read permissions on a share call sambashare. I connected to that using a null session of smbclient:
smbclient //192.168.187.76/sambashare -N
I was able to login with the null session and found mailsent.txt and a wordpress.bkp.zip. I catted out the mail file and found a message to someone named Daisa that their site was now ready, and to not “forget your secret, my babygirl ;)”.. Not sure what that means but daisa is probably a user on the system so I added that to my usernames file, and babygirl as a possible password to my passwords file. WordPress.bkp.zip just seemed to be a backup of the wordpress site. I then used enum4linux to enumerate the smb service further and found 2 system users, daisa (as suspected) and agi. Those were added as confirmed users in the usernames file. I then immediately attempted hydra for both users, but failed on both, as well as the babygirl potential password for daisa but failed again, so no ssh access at the moment.
Lets move on to the web server on port 80. There is a messaging form on the web site but really, not much going on. Checking the source code and the usual extensions like robots.txt, .svn and .DS_STORE also revealed nothing. A feroxbuster scan found /assets and /images subdirectories but after searching through those, I also came up with nothing.
Lets move on to the web server running on port 8000. This seems to be pretty simple page with a number of links but they don’t seem to do much. Once again, source code, .svn, .DS_STORE, and robots.txt all revealed no further information. A feroxbuster scan found an /admin page which seems to be a login for the koken cms. I tried daisa:babygirl and gained access!! Those were logged in my creds file as valid creds for the cms.
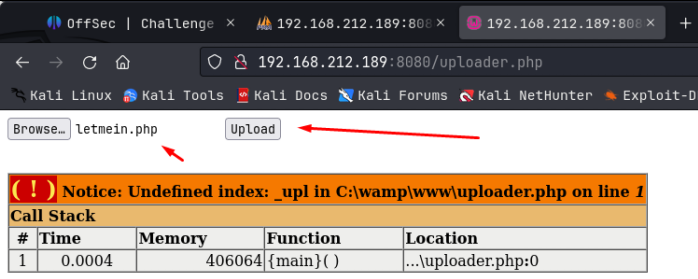
Looking around the cms, I found a button on the lower right side ‘import content’ which allows us to upload files. I then searched searchsploit for koken cms and found an exploit for an Arbitrary File Upload (Authenticated), which we are:

This exploit contains instructions how how to capture the upload in burpsuite and adjust the POST request to bypass the upload restriction and upload the following php web shell:
<?php system($_GET[‘cmd’]);?>
After fiddling around with this, I couldn’t make it work. So instead I uploaded a simple php reverse shell, following the same instructions. Lucky for us, the cms is good enough to even give you a link to where the shell was uploaded to, so we don’t have to chase it down manually!
I setup a pwncat listener, activated the reverse shell, and we have our initial foothold!

Next, I uploaded my enumeration script and ran it. You could manually do everything in my script, but the script makes it easy as it contains all the commands I would run manually, if I didn’t have access to the script. In enumeration, we find that we have no sudo privileges as the www-data user. We find home directories for daisa and agi. The local.txt flag is found in daisa’s home directory as well as a user.txt file. There is no ssh keys and no bash history for either user. The web root is found at /var/www/html. The /etc/passwd file contained no new users other than root and the 2 we already have and is not writable. The /etc/shadow file is also not writable and not accessible. Mysql is running on the localhost on 3306. Checking SUIDs and GUIDs we find that the suid bit is set on php. Cross referencing that with GTFObins shows us a privilege escalation exploit to get a root bash shell:

And now we are root!!
This was a very straightforward and easy box. Good for beginners. The root flag is found at /root/proof.txt.