Heist – Vulnhub

Lets start by gathering our nmap scans. I always do a basic and then a detailed scan.
nmap -T4 -p- 10.0.3.7
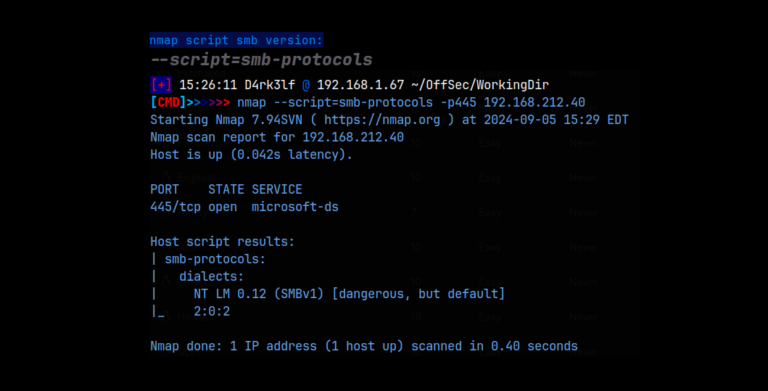
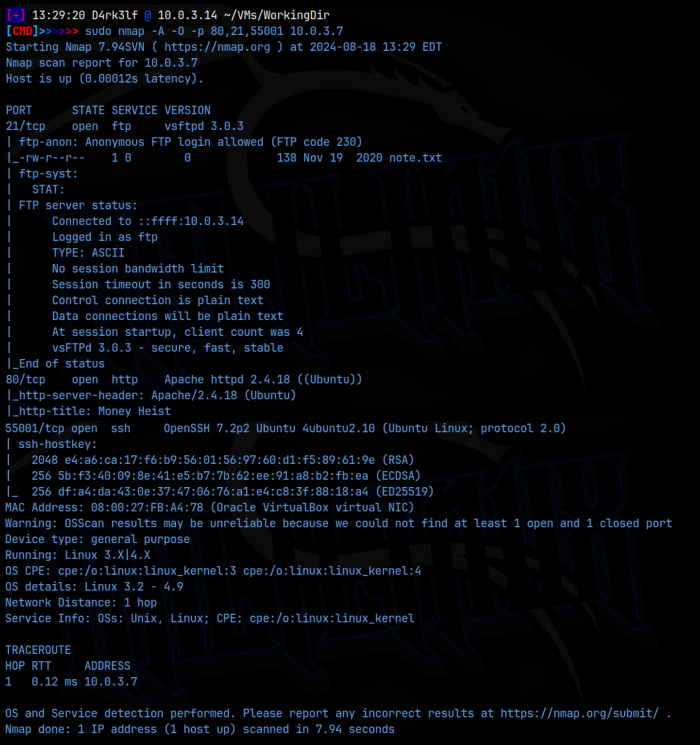
sudo nmap -A -O -p 21,80,55001 10.0.3.7
As we can see from the detailed scan, we have ftp running on 21, ssh running on a non standard port of 55001, and the web server on port 80. It’s important to keep in mind that ssh, normally on 22, is on 55001 on this box. We also find that we are dealing with a Linux machine. FTP is showing that anonymous login is allowed:
Lets start with the anonymous login on ftp. I always use the following command to do this:
ftp -A 10.0.3.7
Using ‘anonymous’ for both the username and password gets us in for an early win. Looking around we find a note.txt file which we download with a ‘get’ command. If we look at the note, it is a message from Angel Rubio who is a partner of Raquel Murillo, and he is asking for help in catching ‘the professor’. We got two possible users then which I added to my usernames list in different formats like 1st name, last name, 1st initial with lastname, etc etc. Just manually building out a list of possible usernames we might be able to use later.
FTP didn’t leave us with much else so I moved on to the web server. I checked robots.txt, .svn, and .DS_STORE extensions but didn’t find anything there. I also checked the source code but again came up with nothing. I then ran a feroxbuster scan of the web page and found /img, /gate, and /robots directories. Starting with /img takes us to a directory listing that contains just 1 file, team.jpg, which I downloaded with wget and tested thoroughly, but didn’t find anything. The /gate directory takes us to a directory listing that contains just 1 file, gate.exe, which I also downloaded with a wget command.
When testing this file, I discovered that even though it is listed as a .exe file, it is actually a .zip file. I used a hex editor to change the file id values to a .zip and then renamed it. If we run a hex dump on the file, we can see an interesting value:

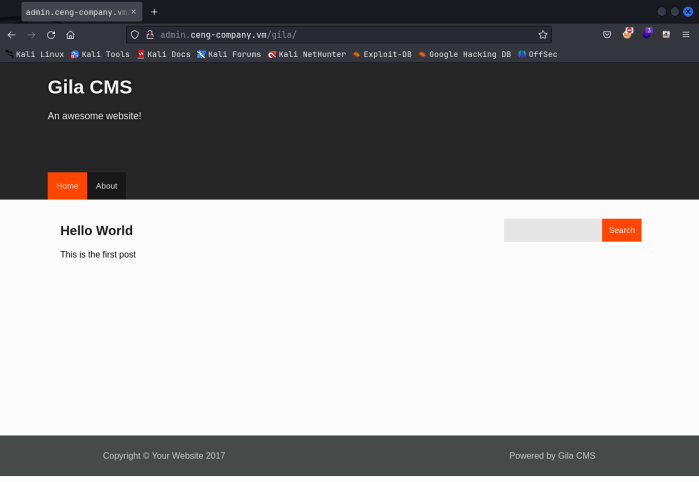
This looks to be another web directory. Having corrected the file hex values, I unzipped the file which gave me another file called ‘note’, and when I catted that out, it gives us the extension /BankOfSp41n. Navigating to that we get the following page:

I then ran another feroxbuster scan on this extension and found bank.jpeg, index.html, login.php, indax.html, avatar.jpgeg and CR3D5.js. I checked the login.php 1st and found that this page is a login to the bank. If we cat out the CR3D5.js file, we are given the login -> anonymous:B1tCh, which I added to the creds file. That indeed gives us access and we are logged in. Backing up for a moment, in the /robots subdirectory, I found another file called tokyo.jpeg which was another file that I had to correct the hex values for. Once I had it corrected for jpeg, I was able to open the image which was just a rabbit hole.
Back at the bank login, if we look at the source code, we find a message in the comments from Arturo Roman, which seems to be a hidden message asking us for help. I added Arturo to the usernames file in the same formats as the other possible users I found.
With nothing else to go on, I decided to try a hydra attack using the Arturo user, as this was the hardest one to find. I had success with that and found his ssh login creds to be -> arturo:corona, which I added to the creds file.
Now that we are in with Arturo, I brought in my enumeration script and ran it. The script shows us that we dont have sudo permissions for the Arturo user nor did it find any ssh keys. It did find additional users from the /etc/passwd file of tokyo, denver, and nairobi, which you can find by manually looking at /etc/passwd. Enumerating the directories, we find that FTP is in the /srv directory. We already found the note.txt in that. In /var we find backups, log, and crash which I made note of. In /etc I found .passwd.swp which seemed very interesting. Checking SUIDs I found that the find binary had a suid bit set. And I found a file in Arturo’s home directory called secret.txt.
Starting with the secret.txt we find that this is another message from Arturo. He is apparently being held as a hostage inside the bank, but we really don’t get any usable information. Arturo did not have any bash history to look at. I then tried to look as the password file in /etc but was denied access. The suid bit being set on the find binary turns out to be out path forward. Looking at GTFObins we see that we can escalate privileges with the suid exploit.
I completed that process and we get access as the Denver user. I then ran manual enumeration as this user. Denver had a file in his home directory called secret_diary that I catted out and discovered yet another web extension:
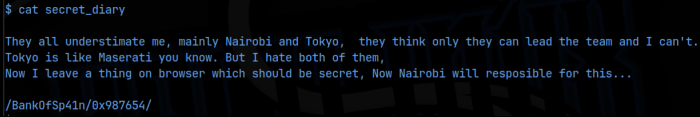
Checking that extension we are taken to a directory listing which contains a key.txt file. I downloaded that and it looks like a message has been morse code encoded. I decoded that and found another encoding, this time something that looks like tap code. That result had to be passed to a rot13 cipher, and then that result had to be passed to an Affine cipher, and we finally arrive at a readable string, ‘iambossbithchhere’ which seems like some sort of password. I tried this with the nairobi user and success! I added that to the creds file.
More manual enumeration, this time as nairobi, and we find a note.txt file in her home directory, which turns out to he an ascii art sniper rifle and message saying that nairobi has been taken out lol. Looking at the SUID bits again I found that gdb had a suid bit set, so I checked out GTFObins for that and found another exploit, allowing python to create an elevated shell. I used that exploit as the nairobi user and I became the tokyo user.
More manual enumeration, this time as tokyo user. I looked at the bash history file in tokyo’s home directory which showed a command of ‘sudo su’, so I know that that tokyo can change to the root user. I tried that hoping I wouldn’t need a password as I didn’t yet have tokyo’s password but that failed. I then checked out the sudo_as_admin_successful file and found a message there that is using the NATO (military) phonetic alphabet to spell out a message:
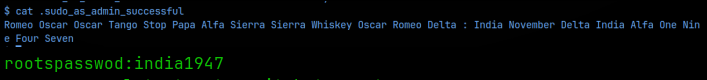
Nice! Now we can switch to the root user. All that’s left to do is find the root flag at /root/proof.txt! It took me quite a long time to figure out the cipher chain. I tried 1st with Cyberchef but that didn’t work for me, so I found another online software that was able to get me to the right string.