DeathNote – Vulnhub
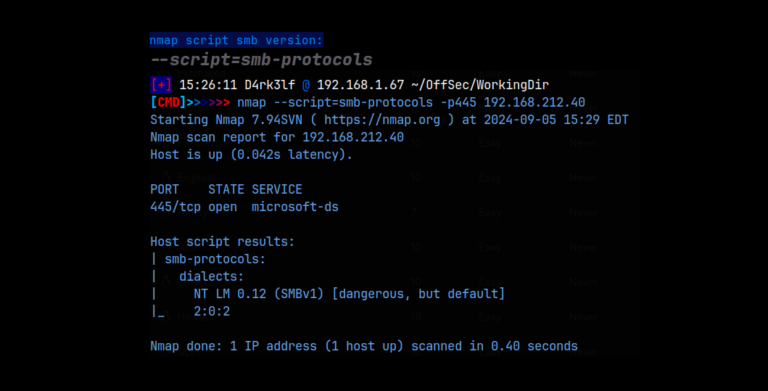
Let’s start by gathering our nmaps scans. I always run a basic nmap scan, as well as a detailed nmap scan:
nmap -T4 -p- 10.0.3.19
sudo nmap -A -O -p 22,80 10.0.3.19
Looking at the detailed nmap scan, we see we have ssh running on port 22 and the website on port 80. We also know that we are dealing with some kind of Linux based machine:

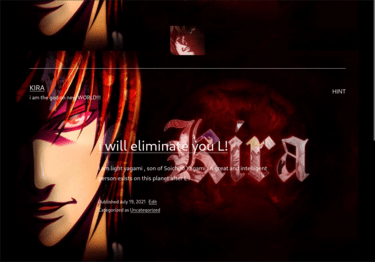
Navigating to the website, re-directs us to deathnote.vuln/worpress. This would not render for me until I added it to the /etc/hosts file. Reloading the page, we see what looks like a main page that has a post from Kira, threatening to eliminate someone name ‘L’. There is also a page link to ‘Hint’. Reading through the page I came up with possible usernames of: kira, light, l, yagami, and soichiro. I also found 2 interesting phrases: ‘i am the god on new WORLD!!’ and ‘i will eliminate you L!’. I added the usernames to my notes as well as the passphrases. There is also a post that says ‘myfav line is iamjustic3’, the ‘iamjustic3’ definitely looks like a password, so that was added to my notes as well. At the bottom of the page, we see that this is powered by wordpress.
When we click on the ‘Hint’ link, it shows a note:

So we know we need to find this notes.txt file. I then started auto-enumeration with Feroxbuster and found the wordpress login page at /wordpress/wp-admin/user. I then ran a quick wordpress scan and found a confirmed user of Kira. Since we have user Kira and a possible password of iamjustic3, I tried to login to wordpress and success! Lucky guess. Checking the users tab shows us that Kira is the admin user; NICE! In the media tab, I found the notes.txt file. Clicking on that gives us the option to copy the file URL to clipboard, then we can paste that in to a wget command and download the file, as seen here:
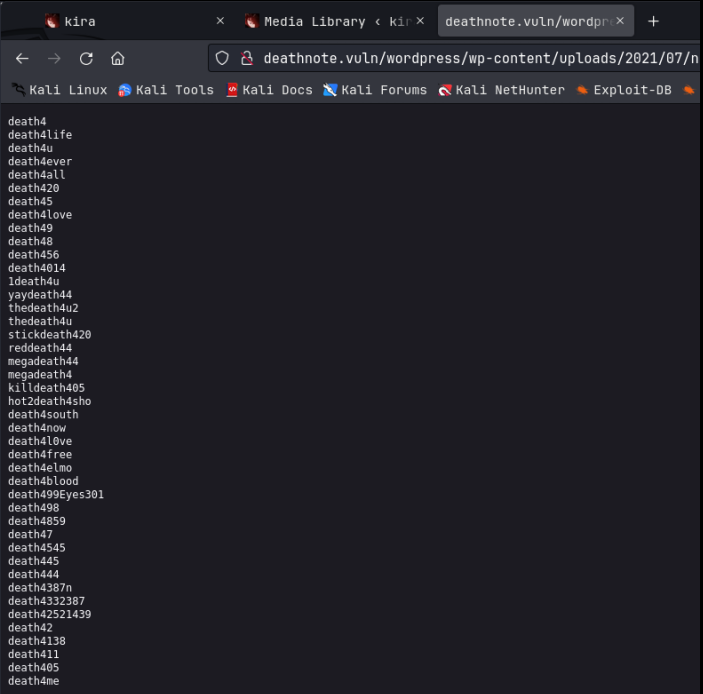
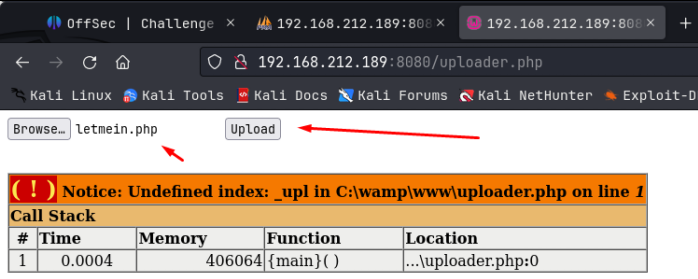
Ooo, looks like a wordlist, possibly we can use this to brute force ssh logins with hydra?? I tried this route with Kira but, no hits. So no ssh at the moment. But we do have admin access to the wordpress page, so my next step was to upload a wordpress reverse shell as a plugin, setup a pwncat listener on 9090, and then activate the plugin:
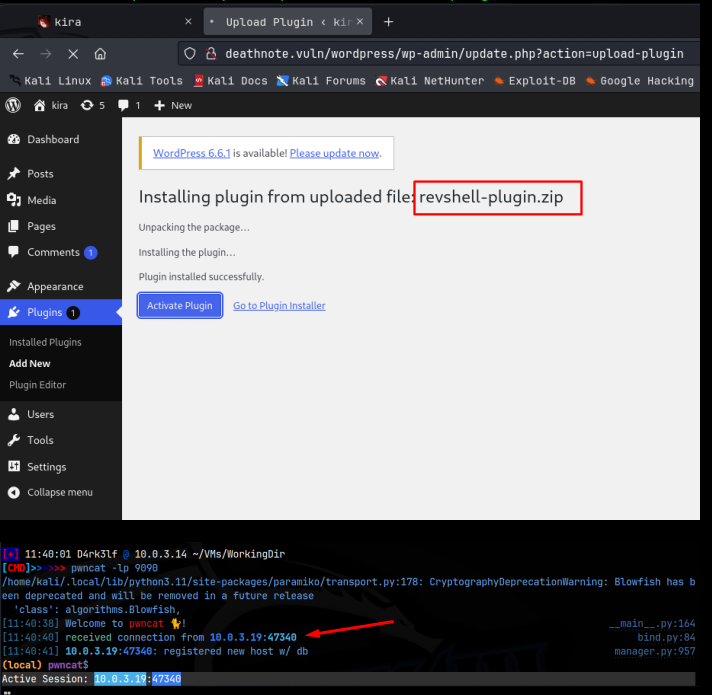
Great! We now have our initial foothold on the machine. I then uploaded my custom enumeration script to the target and ran it. If you manually enumerated though, you would find 3 users in the /etc/passwd file; root,l, and kira. Interesting that the user ‘l’ is just a single letter. I then immediately ran another hydra attack on that user, using the wordlist we found, and success! We got the creds as ‘death4me’:

Looking in the /opt directory, I found 2 subdirectories, /fake-notebook-rule and /kira-case. /fake-notebook-rule contained 2 files, hint and case.wav. I download both of those. Hint didn’t turn out to be of much use as it just referenced the case.wav file. That file however is a bit tricky. It’s labeled as a .wav file, which I tried to play, but got nothing. Running file on that returns that it is actually and ascii text file, so I just catted it out and it gives us a bunch of 2 digit hex codes. I then ran the following commands:
cat case.wav | xxd -r -p > output.bin; cat output.bin
We get a short base64 encoded string, and then decoding that we get Kira’s creds! Nice! Now we have ssh creds for both kira and l. In the /var directory, I found a file called ‘misa’ but that was not useful either, just a short message about someone named misa. I then moved on to the web root at /var/www/deathnote.vuln/ and found a file called robots.txt which I could not access from the URL when checking that on the website, as well as a file called important.jpg. Robots.txt contained a message that something was hidden in important.jpg. I then ran the file command on important.jpg and indeed, it’s not a jpeg file, it’s an ascii file, so I catted that out and it said that there was a login username of user.txt, and to try to find a password. No idea what service the user.txt is for yet.
When enumerating the networking, I found that mysql was running on 127.0.0.1:3306 and that I had access to the wp-config.php file at /var/www/deathnote.vuln/wordpress/wp-config.php. I checked that file and found database creds for the ‘l’ user. I used those to login to mysql and searched the wp_users database and found kira and a hash but I was able to crack it, and I suspected that it was probably just the hash of kira’s password which we already know:
The next step was to login with the ssh creds for both l and kira and see what I could find. In kira’s home directory, I found a file called kira.txt which was a base64 encoded string, that when decoded, had a message to ‘protect L or Misa’. I already found the files that was referencing so I then checked the sudo permissions and found that kira had unlimited sudo permissions on the machine. From there, it was a simple ‘sudo su’ and we are root!! All that’s left to do is find the flag at /root/root.txt.
I also logged in as the ‘l’ user and found the user.txt file referenced earlier. That file contained a brainfuck encoded string which I decrypted as:

This didn’t turn out to be of much use either. Check back soon for the video walkthru!!