Algernon – Offsec PG Practice
Lets start by gathering our nmap scans. I always do a basic nmap scan and then a detailed nmap scan based off the ports returned:
nmap -T4 -p- 192.168.238.65
sudo nmap -A -O -p 21,80,139,445,9998 192.168.238.65
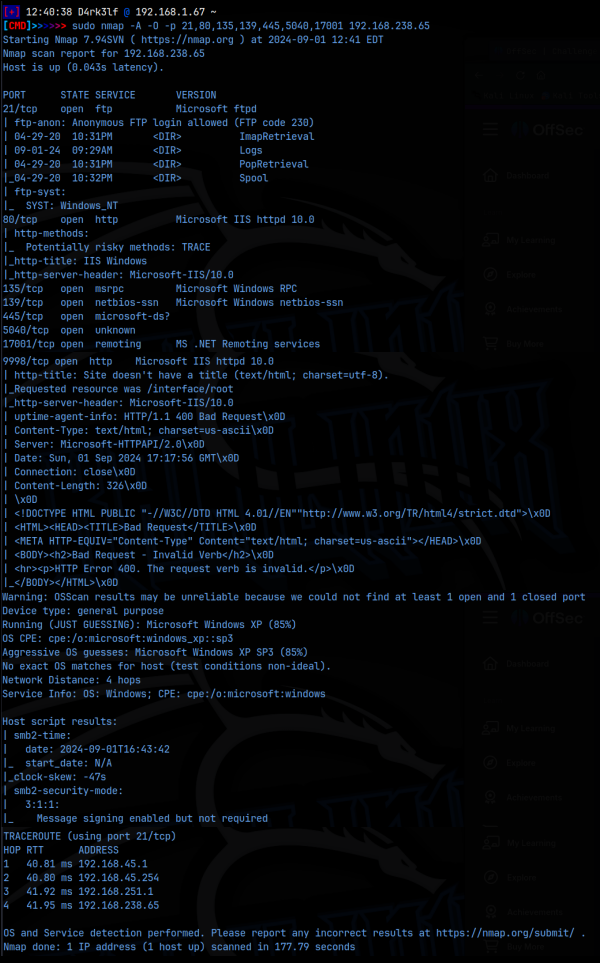
As we can see from the scan, we have ftp running on 21 that is saying anonymous login allowed, we have a web server on port 80 and another on 9998, and then we have smb on 139/445.
I 1st tried smb but null sessions were not permitted. I was able to logon to ftp and there were a couple directories we could navigate to, but after thoroughly checking that, I couldn’t find anything useful. I then began to check the web server on port 80, but it just loaded the standard windows page, and a feroxbuster scan found nothing.
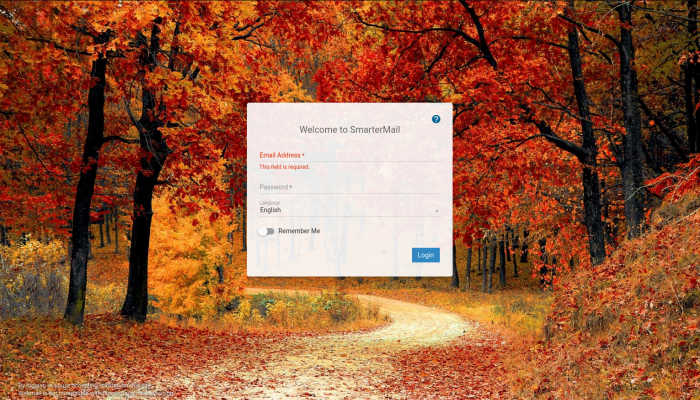
I then moved on to the web server on port 9998 and was directed to this login page for the SmarterMail application:

I checked the source code but didn’t find anything useful. I also check for robots.txt but got a 404 error on that. A feroxbuster scan found interface, about, affsignin.aspx (which wouldn’t load), and a few other extensions but the login page was the only thing I could reach.
I ran a searchsploit for SmarterMail and found a number of exploits, specifically one for RCE. I checked around and could not find a version so I hoped that this would work. After pulling down a mirror, I checked out the .py file and determined that it uploaded a reverse shell. I had to make changes to the target host IP, and the listener host IP and port. Once done, I setup a pwncat listener and ran the .py file. I did get a connection, but it wasn’t a full shell and pwncat kept dropping it. I then decided to use a netcat listener and ended up getting a connection!
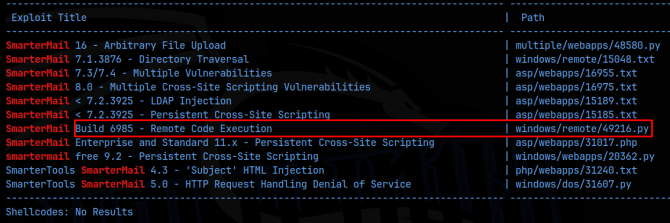
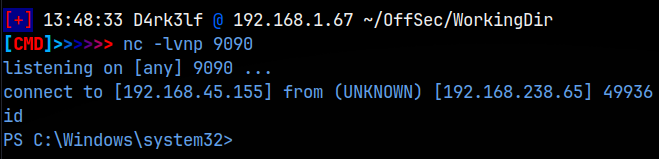
Great!, that was easy, and a little lucky considering I didn’t have the version information and had no idea if it would work or not.
With our initial foothold completed, it’s time to start enumerating. I 1st ran ‘whoami’ and we were NT Authority/System!! We already had a root shell thanks to the exploit.
All I had to do was navigate to C:\Users\Administrator\Desktop and get the flag! I don’t think I’ve seen an easier box. The exploit took care of everything for us.