Raven 1 – Vulnhub
Lets start by gathering up the nmap scans. I always do a basic and then detailed nmap scan:
nmap -T4 -p- 10.0.3.17
nmap -A -O -p 22,80,111,49963 10.0.3.17
As we can see from the detailed nmap scan, we have ssh running on port 22, the web server on port 80, and rpc on what appears to be both 111 and 49963:
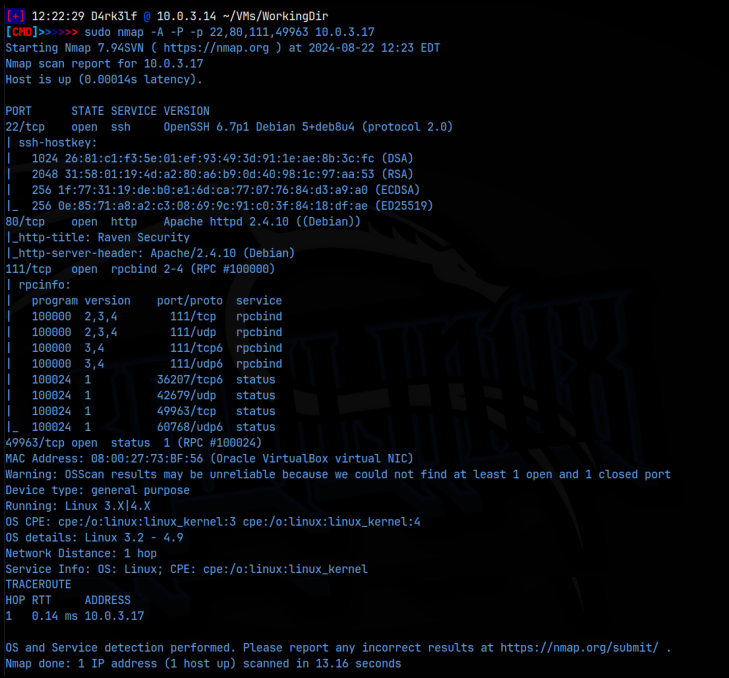
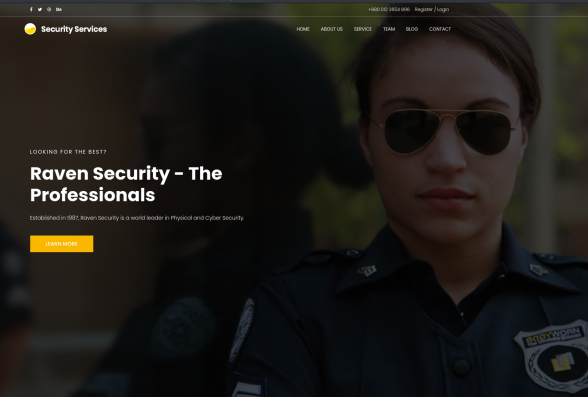
We can also tell that we are dealing with a Linux machine. Since we don’t have any information for ssh, I started on the web server. Navigating to the web page, we are greeted with a page that seems to be associated with a security company. There are links about the company at the top right, and a link to their blog page. I started with some manual enumeration looking at the source code, robots.txt, .svn and .DS_STORE extensions. Flag 1 of 4 is found in the source code of the services tab.
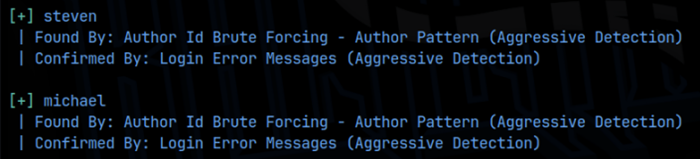
I then began a feroxbuster scan of the site and found the wordpress login page at /raven.local/wordpress/wp-login.php. In order for this to load correctly, I added raven.local to the /etc/hosts file. This also allowed the blog page to load correctly. Further, I found a /vendor extension as well. Since we now know that we are running wordpress, I ran a wp-scan and found 2 associated users, steven and michael:
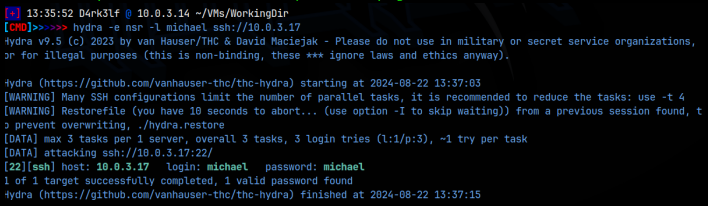
I couldn’t find any passwords so the next step was to try and brute force the passwords using hydra. I 1st ran this with rockyou.txt but I wasn’t getting any hits, so I stopped it and ran it with the -e nsr flag. I got a hit on michael for the michael user; essentially the username was the password as well.
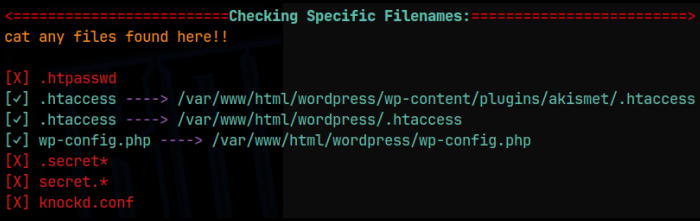
With the initial foothold on the machine, I then upload my enumeration script with a wget command, and ran it. Had you done manual enumeration, you would have found that there are 2 users, steven and michael, from the /etc/passwd file. Looking at the /var directory, we find Flag 2 of 4. My enumeration script showed that the wp-config.php file was located at /var/www/html/wordpress/wp-config.php, but you could of found this by manually looking around the /var directory as well:
When I opened that file, I found creds for the mysql database being: root:R@v3nSecurity. I logged in to the database and began looking around. I found Flag 3 of 4 in the wp_posts table. I also found usernames and password hashes in the wp_users table:

I used John the Ripper to crack steven’s hash as pink84. I was then able to ssh in as steven. Checking steven’s sudo privileges shows that he is able to run /usr/bin/python as sudo with no password required. GTFObins shows an exploit for that using the import os module and then calling /bin/bash. Running that with sudo permissions results in a shell with the elevated privileges of the user, in this case sudo being root privileges, which gives us the root shell!
This was really a pretty easy box. All that’s left to do is get Flag 4 of 4 which is found in the /root/root.txt file.